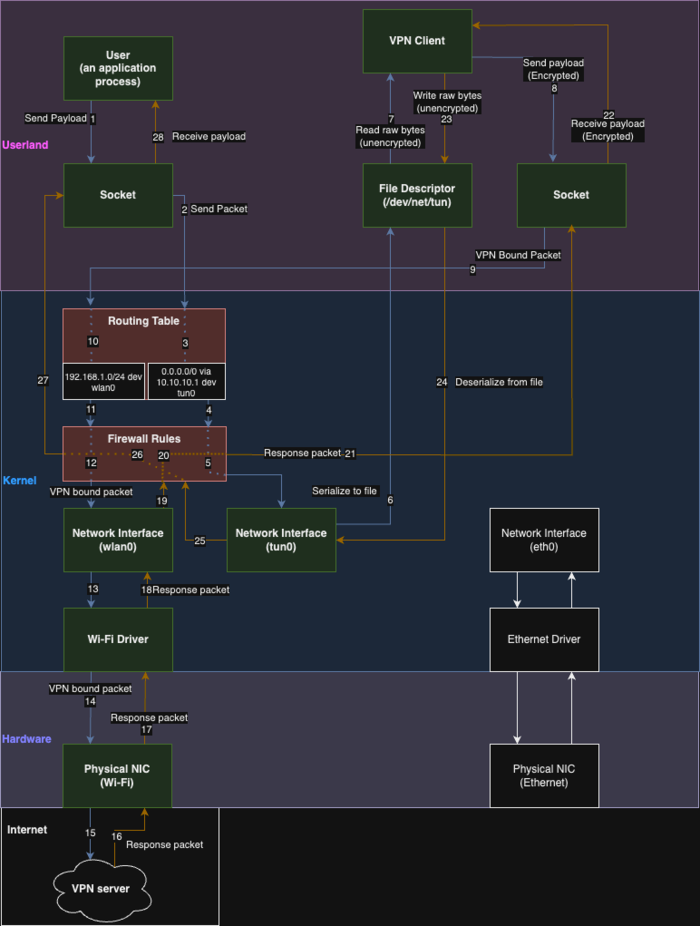
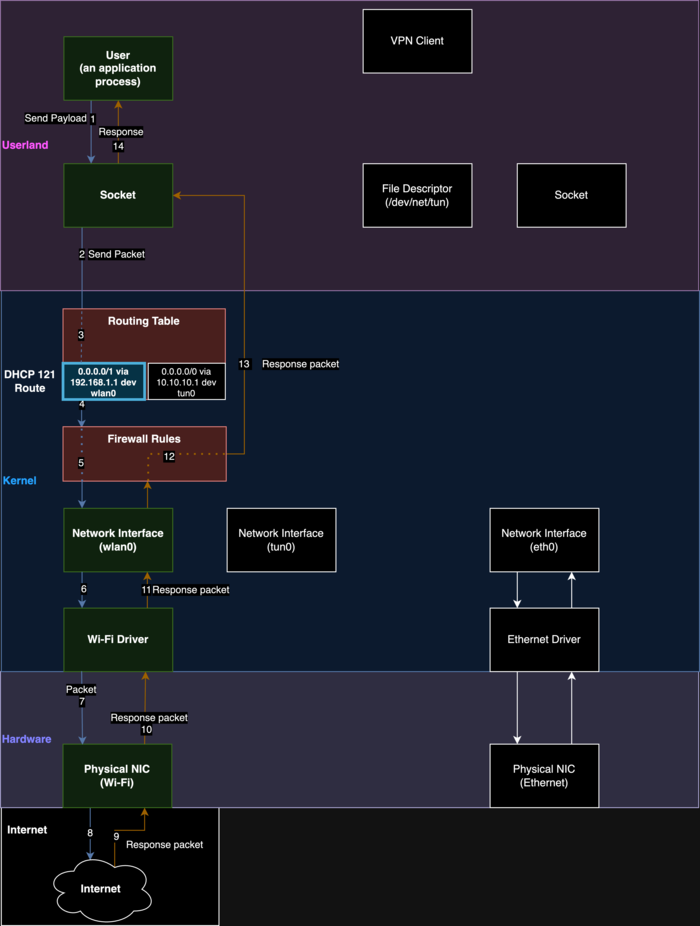
For the attention of the public proposed attack method TunnelVision, which allows, if you have access to a local network or control over a wireless network, to redirect the victim’s traffic to your host, bypassing the VPN (instead of sending it through the VPN, the traffic will be sent in the clear without tunneling to the attacker’s system). The problem affects any VPN clients that do not use isolated network namespaces when routing traffic to the tunnel or do not set packet filter rules when setting up the tunnel that prohibit routing VPN traffic through existing physical network interfaces.
The essence of the attack is that the attacker can launch his own DHCP server and use it to send information to the client to change routing. In particular, an attacker can take advantage of the DHCP protocol option 121 (RFC-3442, adopted in 2002), designed to transmit information about static routes, to make changes to the routing table on the victim’s machine and direct traffic bypassing the VPN. Redirection is carried out through setting a series of routes for subnets with the /1 prefix, which have a higher priority than the default route with the /0 prefix (0.0.0.0/0); accordingly, instead of the virtual network interface set for VPN, traffic will be directed through the physical network interface to the attacker's host on the local network.
Advertisement
The attack can be carried out on any operating system that supports 121 DHCP options, including Linux, Windows, iOS and macOS, regardless of the VPN protocol (Wireguard, OpenVPN, IPsec) and cipher suite used. The Android platform is not susceptible to attack because does not process option 121 in DHCP. In this case, the attack allows you to gain access to traffic, but does not allow you to wedge into connections and determine the content transmitted using secure application-level protocols, such as TLS and SSH; for example, the attacker cannot determine the contents of requests over HTTPS, but can understand which they are sent to the servers.
To protect against an attack, you can prohibit at the packet filter level the sending of packets addressed to the VPN interface through other network interfaces; block DHCP packets with option 121; use VPN inside a separate virtual machine (or container), isolated from the external network, or use special tunnel configuration modes, using network namespace. To experiment with carrying out an attack published a set of scripts.
It may be noted that the idea of local routing change is not new and has previously been commonly used in attacks aimed at spoofing a DNS server. In a similar TunnelCrack attack that rerouted traffic through a replacement default gateway, the problem affected all tested iOS VPN clients, 87.5% of macOS VPN clients, 66.7% of Windows, 35.7% of Linux, and 21.4% of Android. In the context of VPN and DHCP, the method was also mentioned earlier, for example, it is dedicated to one of the reports at last year's USENIX 2023 conference (a study found that 64.6% of 195 VPN clients tested were susceptible to attack).
To substitute routes, it was previously also proposed to use a specially designed USB key that simulates the operation of a network adapter, which, when connected to a computer using DHCP, declares itself as a gateway. In addition, when there is control over the gateway (for example, when the victim connects to an attacker-controlled wireless network), a technique has been developed to inject packets into the tunnel that are perceived in the context of the VPN network interface.
Advertisement
Data streams when using VPN:
Thanks for reading: