The latest versions of the Raspberry Robin malware have become more secretive and use exploits for recent 1-day bugs that are used against vulnerable systems.
According to experts Check Pointhackers actively use 1-day vulnerabilities in their attacks, that is, problems that have already been fixed by developers, but for some reason these fixes have not yet been deployed to all clients, or not all users have installed them
Advertisement
Raspberry Robin operators have used at least two exploits for 1-day vulnerabilities recently, and analysts believe that the malware operators either have the ability to create their own exploits or have sources that provide them.
Recall that Raspberry Robin is a dropper with the functionality of a worm. It primarily spreads through removable storage devices, including USB flash drives, to gain a foothold on infected systems and make it easier for hackers to deploy additional payloads. Previously, he was associated with such groups as FIN11, Evil Corp and Clop.
Raspberry Robin is constantly evolving and acquiring new features, detection evasion techniques, and distribution methods. For example, it has previously been seen to use fake payloads to confuse researchers.
According to Check Point, Raspberry Robin activity has increased since October 2023, with large-scale attacks affecting systems around the world.
Advertisement
A notable change in recent campaigns has been the use of Discord to deliver malicious archived files to targets, likely after sending phishing links via email. Such archives contain a signed executable file (OleView.exe) and a malicious DLL file (aclui.dll), which is loaded when the executable file is launched, thereby activating the Raspberry Robin on the system.
When Raspberry Robin is first launched on a victim's computer, it automatically attempts to escalate privileges using various 1-day exploits. For example, Raspberry Robin uses exploits for local privilege escalation vulnerabilities in Microsoft Streaming Service Proxy and Windows TPM Device Driver (CVE-2023-36802 and CVE-2023-29360).
It is noted that in both cases, the malware exploited vulnerabilities using exploits unknown at that time, less than a month after the public disclosure of information about these problems (June 13 and September 12, 2023).
At the same time, according to analysts Cyfirmaan exploit for CVE-2023-36802 that allows privilege escalation to SYSTEM, has been available for purchase on the dark web since February 2023, seven months before Microsoft fixed the issue.
All this suggests that Raspberry Robin operators buy 1-day exploits from third-party suppliers almost immediately after they become available (because the cost of 0-day exploits is too high). Check Point reports that this theory is supported by the fact that the Raspberry Robin exploits were deployed as external 64-bit executables and did not have the heavy obfuscation that is typical of such malware.
The researchers conclude that Raspberry Robin will likely continue to add new exploits to its arsenal that are not yet publicly available.
The researchers' report also notes a number of improvements implemented in the latest variants of Raspberry Robin, including new mechanisms for anti-analysis, detection evasion and lateral movement.
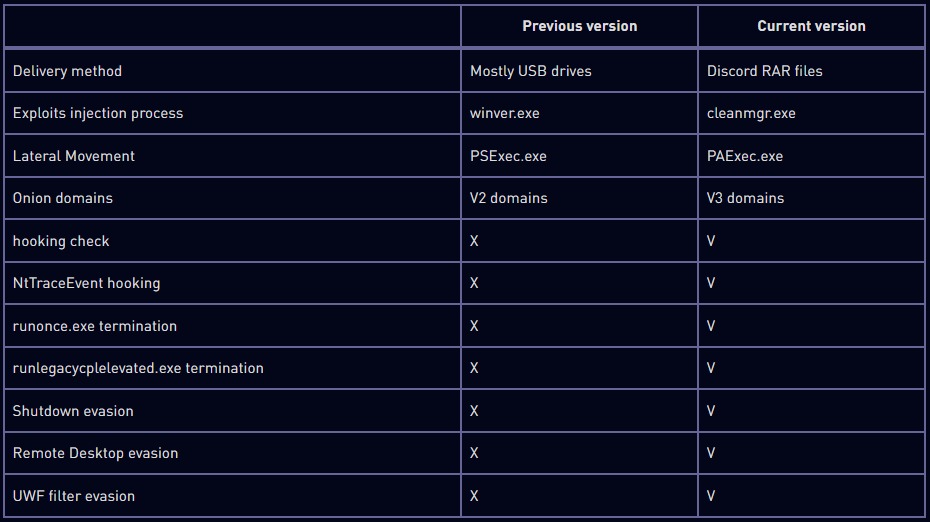
For example, to bypass OS security and protection, the malware attempts to terminate certain UAC-related processes, including runlegacycplelevated.exe, and also makes changes to the NtTraceEvent API to bypass Event Tracing for Windows (ETW) detection.
Additionally, Raspberry Robin now checks if certain APIs (GetUserDefaultLangID and GetModuleHandleW) are enabled to detect security monitoring. And to hide the addresses of the command and control servers, the malware first randomly contacts one of 60 hard-coded Tor domains of known sites to make its first communications appear harmless.

