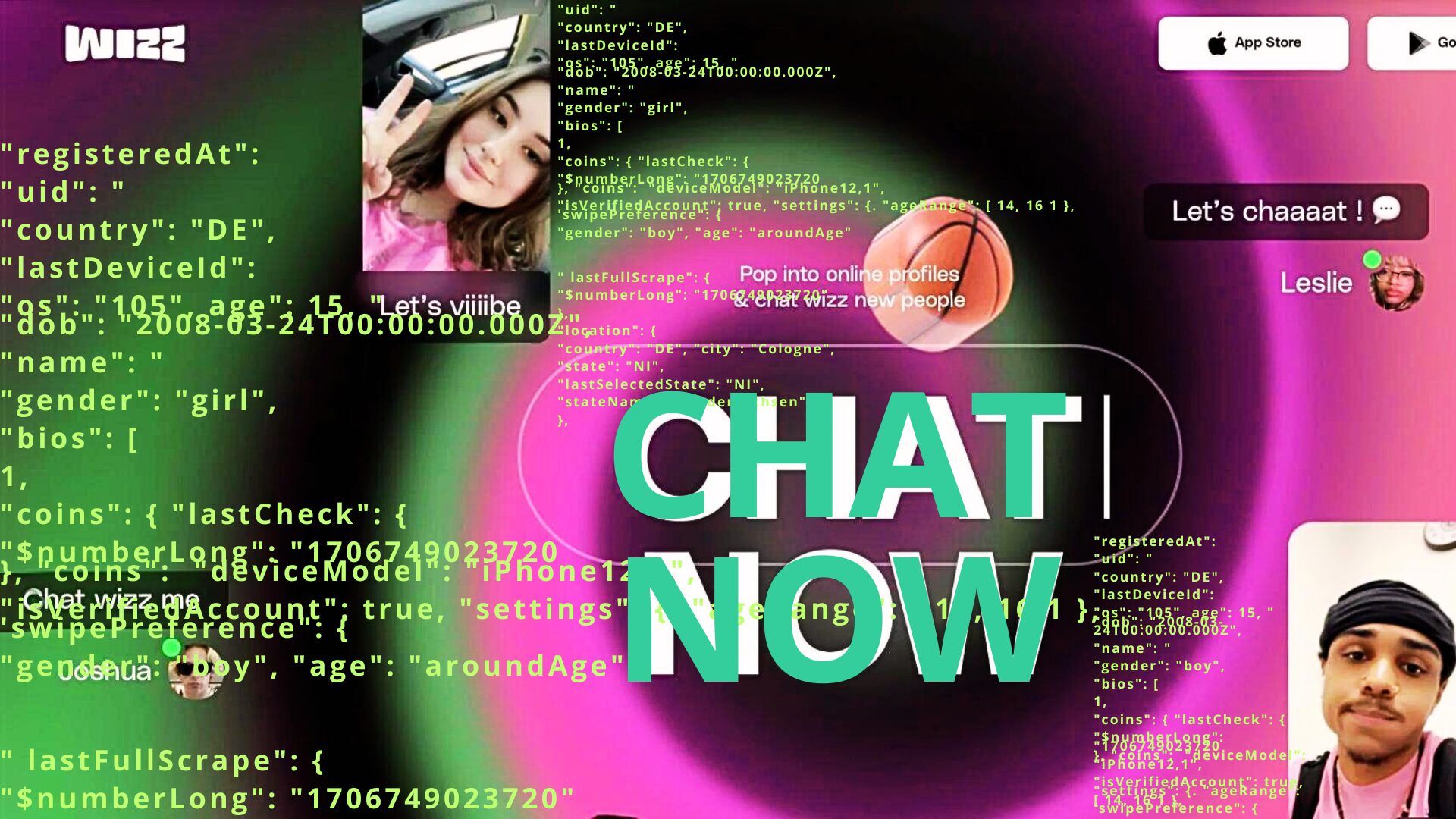
An ethical hacker discovered numerous cybersecurity vulnerabilities on Wizz App, an application singled out for sextortion cases. His research includes captures of private chats.
Obtaining personal information, reading private messages: infiltrating the Wizz App chat application would be child's play, warns a cybersecurity researcher. In an article published on Medium in March 2024, “Aaron”, a cyber expert and ethical hacker, reveals the security vulnerabilities of the platform and shares – anonymized – captures of personal information recovered through these vulnerabilities.
Advertisement
Wizz App rose to prominence last January, when Google Play and the App Store both removed the app from their platforms following sextortion scandals involving minors, recorded by American organizations.
The interface is like any dating app, swiping until you come across a person who interests you. However, the application has found its audience among adolescents, and in the process, the scammers who seek to deceive these young people.
A study of Network Contagion Research Institutea nonprofit organization, notes that “Some victims report being targeted with sexts within minutes of joining the app, suggesting criminals have saturated Wizz “. The goal is to blackmail the person once they have sent compromising photos.
Access to private Wizz App conversations
The cyber expert then recovered a lot of information by scraping the platform, that is to say by automating requests so that the app provides him with information. Aaron even managed to recover private chats by giving the targeted person's user ID to the application. “ By replacing the requests with user identifiers, we can access the entire conversation between these 2 users, with additional private information on their respective accounts », notes the researcher.
Advertisement
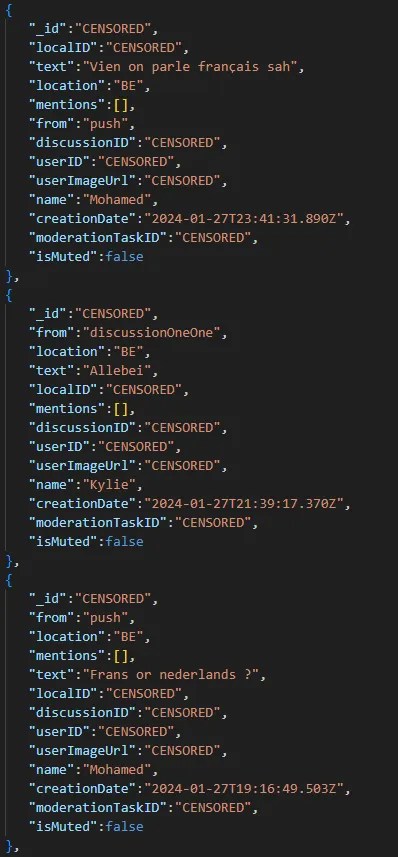
Aaron continued his infiltration into the application script until he accessed Wizz's internal moderation and configuration board. “ I was able to see the tools used by Wizz for mass messaging, moderation and application configuration. »
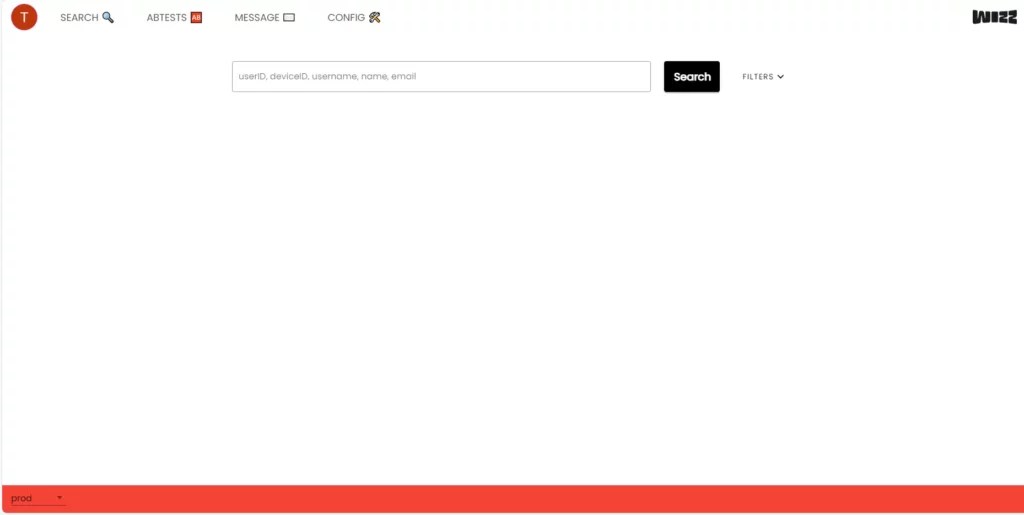

The cyber expert hopes that “ this problem will be resolved quickly and has not yet been exploited by the sexual predators that Wizz has dealt with in the past “.
A circumvention of age limits
“ It was this expert's rare technical skills that allowed him to bypass Wizz's cutting-edge security systems; he exploited an Android flaw which gives experienced hackers the opportunity to decompile the application and thus access private keys and certificates.
Moreover, regarding Android, we only joined the OS last year – compared to 2019 for iOS – to put in place as many security measures as possible because we knew that we would be much more exposed to hackers on Android than on iOS. »
However, all the ethical hacker's maneuvers were carried out from iOS and not from Android, as Wizz claims. In addition, Aaron's scraping is a method that is quite well known to hackers and within the reach of many hackers.
As for blocking the application for banned people, it is always possible to circumvent it by erasing the data from your smartphone or modifying the requests for more competent Internet users.
After our discussions with Wizz, Aaron informed us that the company had started to fix certain vulnerabilities.
*Aaron is a pseudonym used by the ethical hacker.