A group of scientists from Tsinghua University (China) spoke about a new method of DDoS attacks, which was called DNS Bomb. In this case, DNS traffic is used to organize powerful DDoS attacks.
In fact, DNSBomb is a new variation of an attack that was twenty years old. Thus, in 2003 it was published study, which described a DDoS attack using TCP pulses. These attacks use repeated short bursts of large volumes of traffic to impact the target system or service. Such pulses can last up to several hundred milliseconds, occurring every few seconds, and the entire attack can last several hours or days. Typically, pulsed DDoS attacks are more difficult to detect.
Advertisement
DNSBomb takes the same approach, but in a different implementation: it exploits DNS software and a modern DNS server infrastructure, including recursive resolvers and authoritative nameservers.
Essentially, DNSBomb works by sending a slow stream of specially crafted DNS queries to DNS servers, which forward the data, grow the packet sizes and accumulate it, then release it all at once as a powerful burst of DNS traffic aimed directly at the target.
The researchers write that in tests they used DNSBomb against 10 common DNS programs and 46 public DNS services, and achieved an attack with a capacity of up to 8.7 Gbps. In this case, the original DNS traffic was amplified to 20,000 times its original size.
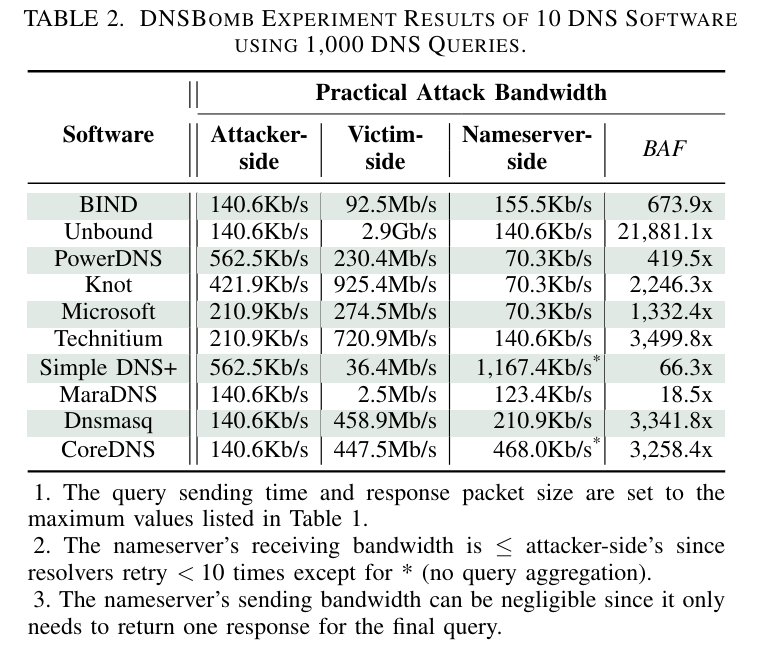
Advertisement
The attack ultimately results in complete packet loss or degraded quality of service on both stateless and stateful connections (TCP, UDP, and QUIC).
“We conclude that any system or mechanism that can combine something (such as DNS and CDN) can be used to create bursty DoS traffic,” the study authors write.
Scientists say they have notified all affected parties about the problem, and 24 organizations are already working on fixes or have released patches. At the same time, among the affected organizations are the most famous DNS providers in the world.
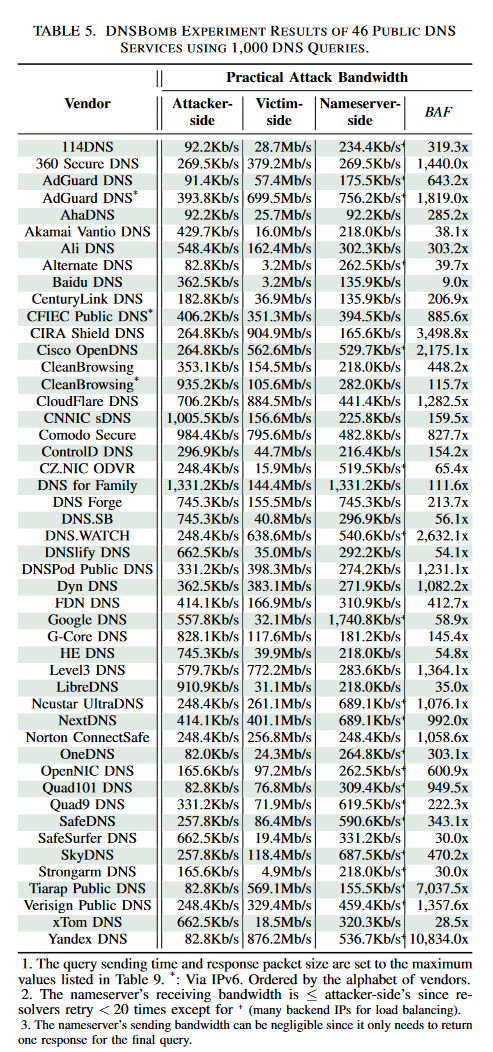
DNSBomb issue has been assigned a major CVE identifier CVE-2024-33655as well as a number of other identifiers associated with specific DNS solutions:
Experts plan to reveal more detailed information about the problem at the IEEE Symposium on Security & Privacy event, which is taking place in San Francisco this week.
