Sucuri analysts warnedthat the previously unknown Sign1 malware infected more than 39,000 sites over the past six months. Visitors to such hacked resources experience unwanted redirects and pop-up ads.
Researchers discovered this campaign when a strange pop-up ad began appearing on the website of one of Sucuri's clients. It turned out that criminals inject malware into custom HTML widgets and legitimate plugins on sites running WordPress, so as not to modify the WordPress files themselves.
Advertisement
The investigation showed that the mentioned Sucuri client was hacked using brute force, but the researchers did not write how the compromise occurred on other hacked sites. Judging by previous attacks on WordPress resources, it can be assumed that a combination of brute force and exploitation of vulnerabilities in popular plugins was used to gain access to sites.
Once the attackers gain access to the victim’s website, they use custom WordPress HTML widgets or install a legitimate plugin Simple Custom CSS and JS to inject malicious JavaScript code.
Sign1's analysis showed that the malware uses time-based randomization to generate dynamic URLs that change every 10 minutes to bypass blocks (domains are registered shortly before being used in attacks, so they are not on any blacklists). These URLs are then used to obtain subsequent malicious scripts that are already executed in the visitor's browser.
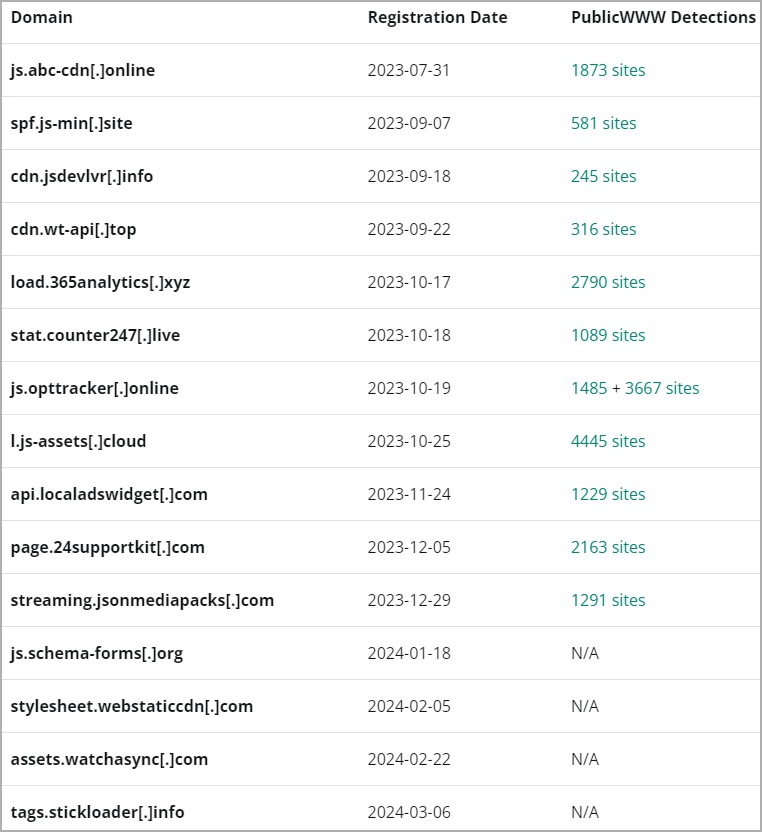
It is noted that initially the attackers’ domains were hosted on Namecheap, but now the hackers have switched to HETZNER and Cloudflare to obfuscate IP addresses.
Advertisement
Before execution, the malware checks for the presence of certain referrers and cookies, targeting visitors coming from large sites such as Google, Yahoo, Facebook* and Instagram*, while doing nothing otherwise.
Additionally, the malware creates a cookie in the user's browser so that the pop-up window is displayed only once per visitor. This reduces the likelihood that the owner of the hacked site will be reported to the problem.
The script ends up redirecting visitors to fraudulent sites, such as those with fake CAPTCHAs, that try to trick the user into turning on browser notifications. Such notifications deliver unwanted advertisements directly to the desktop of the victim's operating system.
Sucuri warns that Sign1 is evolving, and the number of infections increases every time a new version of the malware is released. Thus, over the past six months, the company’s scanners have detected infections on 39,000 sites, and the latest wave of attacks, which has been going on since January 2024, has already affected more than 2,500 resources.

* Belongs to the Meta company, which is recognized as an extremist organization and is banned in the Russian Federation.
