A vast database has been released, revealing the activity of a Chinese spy company. Surveillance tools, infiltration programs as well as targets, including two French ones, were revealed.
Hundreds of Chinese documents were exposed for no apparent reason on February 18 on Github, a public platform for developers. Very quickly, all the cyber experts looked into on these files which were quickly identified as a database of a Chinese spy company. The company in question, called I-Soon, provides tools, programs and services to the Chinese government. According to the group of geopolitics and security researchers “NATTO”I-Soon was founded by a patriotic hacker, CEO Wu Haibo (吴海波), aka Shutdown, in the cyber world.
Advertisement
Analysis of cybersecurity companies SentinelOne And Malwarebytes found that I-Soon develops software capable of compromising devices running Windows, macOS, Linux, iOS and Android. The attack program on Android can apparently retrieve and send a user's entire messaging history from Chinese chat apps, as well as Telegram.
The Chinese team claims to have accessed government services in India, Thailand, Vietnam and South Korea, and a NATO system. Spying equipment to corrupt wifi access was also revealed.
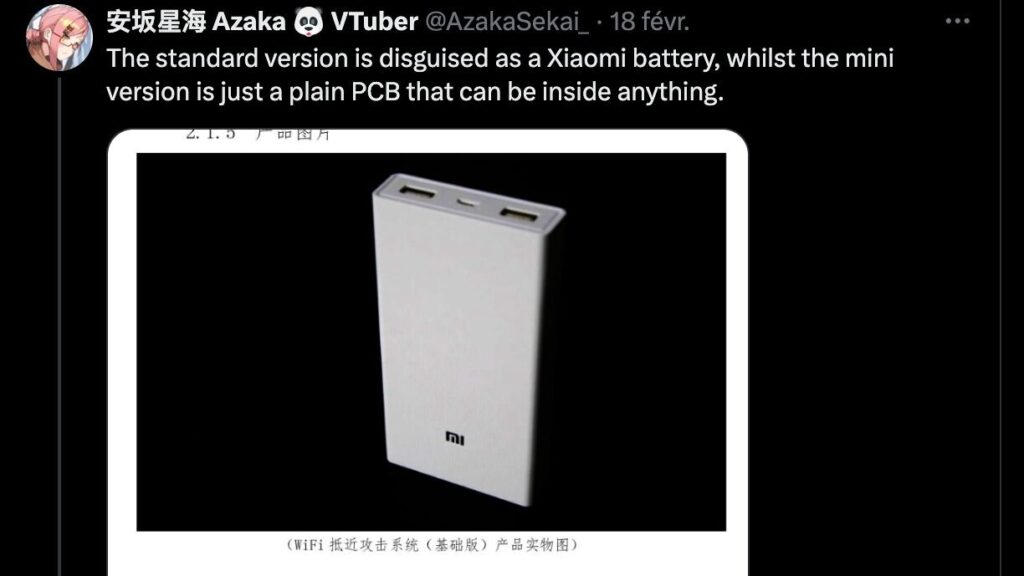
Tools to spy on emails and calls
The ethical hacker Baptiste Robert, at the head of the company Predicta lab, looking into this leak and tells us that the famous “Shutdown” is a veteran of the Chinese army. “ He set up a team of around thirty hackers and engineers to search for zero-day flaws (undiscovered vulnerabilities) on behalf of China. They have tools to replicate a mailbox, retrieve calls and then analyze conversations », Explains the cyber expert. “ The two founders of I-Soon left public traces, such as Twitter or Linkedin accounts. We even found an email address », he adds.
Baptiste Robert brings them closer to a group of Chinese hackers APT41, also known as Double Dragon, several members of which are wanted by the FBI.
Advertisement
In one of the documents published on Github, we can find a target list to spy on. Two French names appear, Jean-Louis Rocca and Vincent Fertey. The first is a famous researcher on China at Science-Po, the second is the former director of Sciences-Po Paris, Le Havre campus. “ This is not surprising, we know that China has long targeted researchers who work on China », adds Baptiste Robert.

Who is behind this data leak?
How could such a sensitive database end up in a platform open to all? “ There is an intention to harm, it cannot be an accident », Says Thomas Segura, cyber expert for the company GitGuardian. “ The leak was not published on an obscure darknet forum where insiders and hackers hang out, but on a site where anyone can access. This means there is a desire to expose their activity, rather than reselling data as cybercriminals typically do “.
Internal leak? Brilliant move by American intelligence? Nothing can be confirmed, but it is certain that this file will be analyzed down to the last line of code by all cyber defense bodies.
